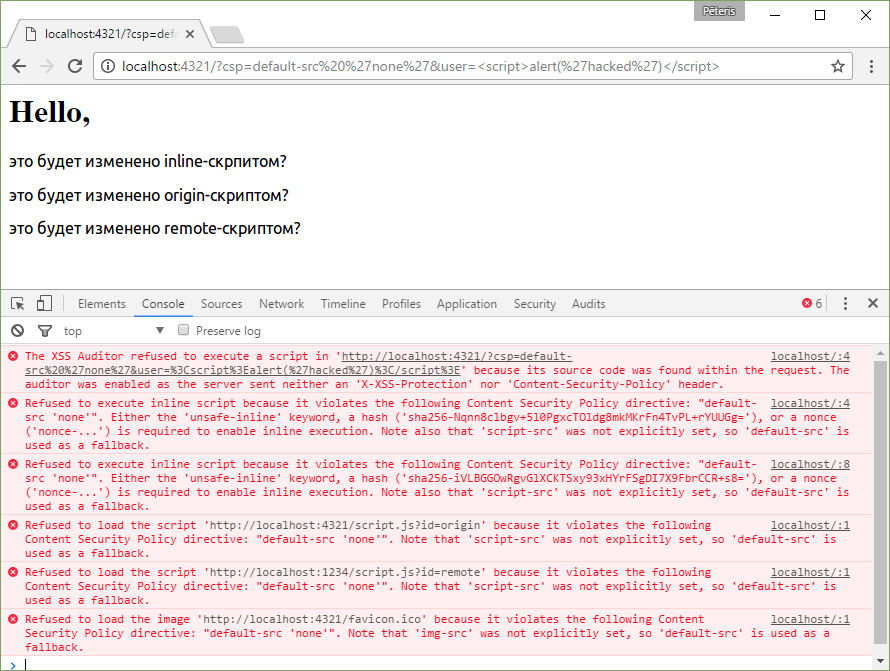
How does the Set-Cookie HTTP response header work. What are the key attributes of Set-Cookie. How can you ensure secure cookie management using Set-Cookie. What are the best practices for implementing Set-Cookie in web applications.
Understanding the Set-Cookie HTTP Response Header
The Set-Cookie HTTP response header is a crucial component in web communication, allowing servers to send cookies to user agents. These cookies can then be sent back to the server in subsequent requests, enabling stateful interactions in the stateless HTTP protocol.
Why is Set-Cookie important? It facilitates various essential web functionalities:
- Session management
- Personalization
- Tracking user behavior
- Maintaining user preferences
How does Set-Cookie work? When a server sends a response with a Set-Cookie header, the user agent (typically a web browser) stores the cookie information. In future requests to the same domain, the browser includes the cookie in the request headers, allowing the server to recognize and respond accordingly.

Key Attributes of the Set-Cookie Header
The Set-Cookie header consists of several attributes that define the cookie’s behavior and security properties. Understanding these attributes is crucial for proper cookie management.
Essential Set-Cookie Attributes
What are the core components of a Set-Cookie header?
- cookie-name=cookie-value: The basic name-value pair defining the cookie
- Domain: Specifies which hosts can receive the cookie
- Path: Indicates the URL path that must exist in the requested URL to send the Cookie header
- Expires or Max-Age: Defines the cookie’s lifespan
- Secure: Ensures the cookie is only sent over HTTPS
- HttpOnly: Prevents JavaScript access to the cookie
- SameSite: Controls how cookies are sent with cross-site requests
How do you properly format a Set-Cookie header? Here’s an example:
Set-Cookie: username=john_doe; Domain=example.com; Path=/; Expires=Wed, 21 Oct 2023 07:28:00 GMT; Secure; HttpOnly; SameSite=StrictEnsuring Secure Cookie Management with Set-Cookie
Security is paramount when dealing with cookies, as they often contain sensitive information. How can you enhance cookie security using Set-Cookie attributes?
- Use the Secure flag to ensure cookies are only transmitted over HTTPS
- Implement the HttpOnly flag to prevent JavaScript access, mitigating XSS attacks
- Utilize the SameSite attribute to control cross-site request behavior
- Set appropriate Domain and Path attributes to limit cookie scope
- Use short expiration times with Expires or Max-Age for sensitive data
Why is the __Secure- prefix useful? It enforces stricter security measures by requiring the cookie to be set with the Secure flag and from a secure (HTTPS) page.
How does the __Host- prefix enhance security? It imposes even stricter rules, requiring the Secure flag, HTTPS origin, no Domain specification, and the Path set to /.
Best Practices for Implementing Set-Cookie in Web Applications
Implementing Set-Cookie effectively requires adherence to best practices. What are some key guidelines to follow?
- Use HTTPS for all cookie transmissions
- Implement proper session management
- Avoid storing sensitive information in cookies
- Use secure prefixes when appropriate
- Regularly rotate session cookies
- Implement proper error handling for cookie-related operations
How can you ensure compliance with privacy regulations? Implement clear cookie policies, obtain user consent when required, and provide options for users to manage their cookie preferences.
Common Challenges and Solutions in Set-Cookie Implementation
Developers often encounter challenges when working with Set-Cookie. What are some common issues and their solutions?
Cross-Domain Cookie Sharing
Challenge: Sharing cookies across different domains.
Solution: Use appropriate Domain attributes and consider implementing server-side solutions for secure cross-domain data sharing.
Cookie Size Limitations
Challenge: Browsers impose size limits on cookies.
Solution: Keep cookie data minimal, use server-side storage for larger datasets, and consider using multiple cookies if necessary.
Third-Party Cookie Restrictions
Challenge: Increasing restrictions on third-party cookies in modern browsers.
Solution: Implement first-party cookie strategies and explore alternative tracking methods like server-side tracking.
Advanced Set-Cookie Techniques for Enhanced Functionality
Beyond basic implementation, Set-Cookie offers advanced techniques for sophisticated web applications. How can you leverage these advanced features?
Multi-Cookie Management
For complex applications, multiple cookies may be necessary. How do you manage multiple Set-Cookie headers?
Set-Cookie: user_id=12345; Secure; HttpOnly
Set-Cookie: session_data=abc123; Secure; HttpOnly; SameSite=Strict
Set-Cookie: preferences=dark_mode; Max-Age=31536000This approach allows for granular control over different types of data and their respective security requirements.
Dynamic Cookie Generation
How can you generate cookies dynamically based on user interactions or server-side logic?
- Implement server-side logic to determine cookie content
- Use appropriate naming conventions for clarity
- Set expiration based on the nature of the data
- Apply security attributes as needed
Cookie Versioning
For evolving applications, cookie versioning can be crucial. How do you implement cookie versioning?
Set-Cookie: data_v1=old_format; Max-Age=0
Set-Cookie: data_v2=new_format; Secure; HttpOnlyThis technique allows for smooth transitions between different data formats or structures.
Set-Cookie and Modern Web Architecture
As web architecture evolves, so does the role of Set-Cookie. How does Set-Cookie fit into modern web paradigms?
Set-Cookie in Single Page Applications (SPAs)
SPAs often rely on APIs for data exchange. How can Set-Cookie be effectively used in this context?
- Implement proper CORS (Cross-Origin Resource Sharing) configurations
- Use HttpOnly cookies for sensitive data like authentication tokens
- Consider using JWT (JSON Web Tokens) in combination with cookies for stateless authentication
Set-Cookie in Microservices Architecture
In a microservices environment, cookie management becomes more complex. What strategies can be employed?
- Implement a centralized authentication service
- Use API gateways for cookie management across services
- Consider using distributed session management solutions
Future Trends and Developments in Cookie Management
The landscape of web technologies is constantly evolving. What future trends might impact Set-Cookie and cookie management?

Privacy-Focused Developments
With increasing focus on user privacy, how might cookie management evolve?
- Stricter regulations on data collection and storage
- Enhanced user controls for cookie management
- Development of privacy-preserving alternatives to traditional cookies
Integration with Emerging Technologies
How might Set-Cookie adapt to new web technologies?
- Enhanced integration with Progressive Web Apps (PWAs)
- Adaptation to WebAssembly for improved performance
- Evolution to support decentralized web architectures
As web technologies continue to advance, the Set-Cookie HTTP header remains a fundamental tool in web development. By understanding its intricacies, implementing best practices, and staying abreast of emerging trends, developers can ensure robust, secure, and efficient cookie management in their web applications.
The Set-Cookie header, while seemingly simple, plays a crucial role in modern web development. Its proper implementation is essential for maintaining user sessions, personalizing user experiences, and ensuring the security of sensitive data. As web technologies evolve, so too will the mechanisms for managing client-side data, with Set-Cookie continuing to adapt and remain a key player in the web development ecosystem.

In conclusion, mastering the Set-Cookie HTTP header is not just about understanding its syntax and attributes. It’s about comprehending its role in the broader context of web security, user privacy, and application architecture. By leveraging Set-Cookie effectively, developers can create more secure, efficient, and user-friendly web applications that meet the demanding requirements of today’s digital landscape.
Set-Cookie – HTTP | MDN
The Set-Cookie HTTP response header is used to send a cookie from the server to the user agent, so that the user agent can send it back to the server later.
To send multiple cookies, multiple Set-Cookie headers should be sent in the same response.
Warning: Browsers block frontend JavaScript code from accessing the Set-Cookie header, as required by the Fetch spec, which defines Set-Cookie as a forbidden response-header name that must be filtered out from any response exposed to frontend code.
For more information, see the guide on Using HTTP cookies.
| Header type | Response header |
|---|---|
| Forbidden header name | no |
| Forbidden response header name | yes |
Set-Cookie: <cookie-name>=<cookie-value> Set-Cookie: <cookie-name>=<cookie-value>; Domain=<domain-value> Set-Cookie: <cookie-name>=<cookie-value>; Expires=<date> Set-Cookie: <cookie-name>=<cookie-value>; HttpOnly Set-Cookie: <cookie-name>=<cookie-value>; Max-Age=<number> Set-Cookie: <cookie-name>=<cookie-value>; Partitioned Set-Cookie: <cookie-name>=<cookie-value>; Path=<path-value> Set-Cookie: <cookie-name>=<cookie-value>; Secure Set-Cookie: <cookie-name>=<cookie-value>; SameSite=Strict Set-Cookie: <cookie-name>=<cookie-value>; SameSite=Lax Set-Cookie: <cookie-name>=<cookie-value>; SameSite=None; Secure // Multiple attributes are also possible, for example: Set-Cookie: <cookie-name>=<cookie-value>; Domain=<domain-value>; Secure; HttpOnly
<cookie-name>=<cookie-value>Defines the cookie name and its value.

A cookie definition begins with a name-value pair.A
<cookie-name>can contain any US-ASCII characters except for: control characters (ASCII characters 0 up to 31 and ASCII character 127) or separator characters (space, tab and the characters:( ) < > @ , ; : \ " / [ ] ? = { })A
<cookie-value>can optionally be wrapped in double quotes and include any US-ASCII character excluding control characters (ASCII characters 0 up to 31 and ASCII character 127), Whitespace, double quotes, commas, semicolons, and backslashes.Encoding: Many implementations perform URL encoding on cookie values.
However, this is not required by the RFC specification.
The URL encoding does help to satisfy the requirements of the characters allowed for<cookie-value>.Note: Some
<cookie-name>have a specific semantic:__Secure-prefix: Cookies with names starting with__Secure-(dash is part of the prefix)
must be set with thesecureflag from a secure page (HTTPS).
__Host-prefix: Cookies with names starting with__Host-must be set with thesecureflag, must be from a secure page (HTTPS), must not have a domain specified (and therefore, are not sent to subdomains), and the path must be/.Domain=<domain-value>OptionalDefines the host to which the cookie will be sent.
Only the current domain can be set as the value, or a domain of a higher order, unless it is a public suffix. Setting the domain will make the cookie available to it, as well as to all its subdomains.
If omitted, this attribute defaults to the host of the current document URL, not including subdomains.
Contrary to earlier specifications, leading dots in domain names (
.example.com) are ignored.Multiple host/domain values are not allowed, but if a domain is specified, then subdomains are always included.

Expires=<date>OptionalIndicates the maximum lifetime of the cookie as an HTTP-date timestamp.
SeeDatefor the required formatting.If unspecified, the cookie becomes a session cookie.
A session finishes when the client shuts down, after which
the session cookie is removed.Warning: Many web browsers have a session restore feature that will save all tabs and restore them the next time the browser is used. Session cookies will also be restored, as if the browser was never closed.
When an
Expiresdate is set, the deadline is relative to the client the cookie is being set on, not the server.HttpOnlyOptionalForbids JavaScript from accessing the cookie, for example, through the
Document.cookieproperty.
Note that a cookie that has been created withHttpOnlywill still be sent with JavaScript-initiated requests, for example, when callingXMLHttpRequest.or send()
send()fetch().
This mitigates attacks against cross-site scripting (XSS).Max-Age=<number>OptionalIndicates the number of seconds until the cookie expires. A zero or negative number will expire the cookie immediately. If both
ExpiresandMax-Ageare set,Max-Agehas precedence.PartitionedOptional
Experimental
Indicates that the cookie should be stored using partitioned storage. See Cookies Having Independent Partitioned State (CHIPS) for more details.
Path=<path-value>OptionalIndicates the path that must exist in the requested URL for the browser to send the
Cookieheader.The forward slash (
/) character is interpreted as a directory separator, and subdirectories are matched as well. For example, for
For example, for Path=/docs,- the request paths
/docs,/docs/,/docs/Web/, and/docs/Web/HTTPwill all match. - the request paths
/,/docsets,/fr/docswill not match.
- the request paths
SameSite=<samesite-value>OptionalControls whether or not a cookie is sent with cross-site requests,
providing some protection against cross-site request forgery attacks (CSRF).The possible attribute values are:
StrictMeans that the browser sends the cookie only for same-site requests, that is, requests originating from the same site that set the cookie.
If a request originates from a different domain or scheme (even with the same domain), no cookies with theSameSite=Strictattribute are sent.LaxMeans that the cookie is not sent on cross-site requests, such as on requests to load images or frames, but is sent when a user is navigating to the origin site from an external site (for example, when following a link).

This is the default behavior if theSameSiteattribute is not specified.Nonemeans that the browser sends the cookie with both cross-site and same-site requests.
TheSecureattribute must also be set when setting this value, like soSameSite=None; Secure. IfSecureis missing an error will be logged:Cookie "myCookie" rejected because it has the "SameSite=None" attribute but is missing the "secure" attribute. This Set-Cookie was blocked because it had the "SameSite=None" attribute but did not have the "Secure" attribute, which is required in order to use "SameSite=None".
Note: A
Securecookie is only sent to the server with an encrypted request over the HTTPS protocol. Note that insecure sites (http:) can’t set cookies with theSecuredirective, and therefore can’t useSameSite=None.
SecureOptionalIndicates that the cookie is sent to the server only when a request is made with the
https:scheme (except on localhost), and therefore, is more resistant to man-in-the-middle attacks.Note: Do not assume that
Secureprevents all access to sensitive information in cookies (session keys, login details, etc.). Cookies with this attribute can still be read/modified either with access to the client’s hard disk or from JavaScript if theHttpOnlycookie attribute is not set.Insecure sites (
http:) cannot set cookies with theSecureattribute (since Chrome 52 and Firefox 52). For Firefox, thehttps:requirements are ignored when theSecureattribute is set by localhost (since Firefox 75).
Session cookie
Session cookies are removed when the client shuts down. Cookies are session cookies if they do not specify the
Cookies are session cookies if they do not specify the Expires or Max-Age attribute.
Set-Cookie: sessionId=38afes7a8
Permanent cookie
Permanent cookies are removed at a specific date (Expires) or after a specific length of time (Max-Age) and not when the client is closed.
Set-Cookie: id=a3fWa; Expires=Wed, 21 Oct 2015 07:28:00 GMT
Set-Cookie: id=a3fWa; Max-Age=2592000
Invalid domains
A cookie for a domain that does not include the server that set it should be rejected by the user agent.
The following cookie will be rejected if set by a server hosted on originalcompany.com:
Set-Cookie: qwerty=219ffwef9w0f; Domain=somecompany.co.uk
A cookie for a subdomain of the serving domain will be rejected.
The following cookie will be rejected if set by a server hosted on example.com:
Set-Cookie: sessionId=e8bb43229de9; Domain=foo.example.com
Cookie prefixes
Cookie names prefixed with __Secure- or __Host- can be used only if they are set with the secure attribute from a secure (HTTPS) origin.
In addition, cookies with the __Host- prefix must have a path of / (meaning any path at the host) and must not have a Domain attribute.
Warning: For clients that don’t implement cookie prefixes, you cannot count on these additional assurances, and prefixed cookies will always be accepted.
// Both accepted when from a secure origin (HTTPS) Set-Cookie: __Secure-ID=123; Secure; Domain=example.com Set-Cookie: __Host-ID=123; Secure; Path=/ // Rejected due to missing Secure attribute Set-Cookie: __Secure-id=1 // Rejected due to the missing Path=/ attribute Set-Cookie: __Host-id=1; Secure // Rejected due to setting a Domain Set-Cookie: __Host-id=1; Secure; Path=/; Domain=example.com
Partitioned cookie
Set-Cookie: __Host-example=34d8g; SameSite=None; Secure; Path=/; Partitioned;
Note: Partitioned cookies must be set with Secure and Path=/. In addition, it is recommended to use the
In addition, it is recommended to use the __Host prefix when setting partitioned cookies to make them bound to the hostname and not the registrable domain.
| Specification |
|---|
| HTTP State Management Mechanism # sane-set-cookie |
BCD tables only load in the browser with JavaScript enabled. Enable JavaScript to view data.
Compatibility notes
- Starting with Chrome 52 and Firefox 52, insecure sites (
http:) can’t set cookies with theSecureattribute anymore.
- HTTP cookies
CookieDocument.cookie- Samesite cookies explained (web.dev blog)
Found a content problem with this page?
- Edit the page on GitHub.
- Report the content issue.
- View the source on GitHub.
Want to get more involved?
Learn how to contribute.
This page was last modified on by MDN contributors.
Maryland women’s lacrosse struggled to ‘put it together’ during 2023 campaign
Coach Cathy Reese was impressed with several aspects of Maryland women’s lacrosse’s performance despite the team’s loss to Northwestern in this year’s Big Ten title game. To make a run in the NCAA tournament, Reese said the Terps just had to “put it together.”
The Terps went toe-to-toe with the eventual national champions, entering halftime down one goal in a back-and-forth battle. The second half was a much different story, with the Wildcats outscoring Maryland 7-3.
Many coaches make similar statements as Reese in the early and middle parts of each season — but this wasn’t March, it was May, and the clock was ticking for the Terps.
It finally looked like the Terps put it together in the second round of the NCAA tournament, leading No. 7 James Madison by four with less than 10 minutes remaining. Then, Maryland faltered, allowing five unanswered goals and ending the 2023 campaign with an uncharacteristically early exit.
Then, Maryland faltered, allowing five unanswered goals and ending the 2023 campaign with an uncharacteristically early exit.
This season, Maryland showed flashes of why it entered the season ranked No. 2 in the country, but the team’s inconsistency and inability to put a full 60 minutes together made it fail to fit its billing. The seven losses tied Maryland’s 2021 squad for the most with Reese at the helm. The two seasons are the only times Reese’s squad didn’t reach the Elite 8.
Outside the draw circle, where Shaylan Ahearn led the Terps to the fourth-highest draw percentage in the country, Maryland was up-and-down all season.
Much of the preseason hype revolved around Maryland’s defense. The Terps allowed the second-fewest goals per game in 2022 and looked to be even better on paper. Abby Bosco returned for her final year and Reese added All-American Princeton transfer Marge Donovan. Kennedy Major and Clancy Rheude also debuted after missing the 2022 season because of injuries. But Maryland’s self-proclamation as ‘Defender U’ because of its strong defenders had an early reality check when it was outclassed in February by then-No. 4 Syracuse 20-11. The Terps didn’t allow a 20 goal outing in all of 2022, where opponents reached double digits in just four of their 21 contests.
But Maryland’s self-proclamation as ‘Defender U’ because of its strong defenders had an early reality check when it was outclassed in February by then-No. 4 Syracuse 20-11. The Terps didn’t allow a 20 goal outing in all of 2022, where opponents reached double digits in just four of their 21 contests.
[Maryland women’s lacrosse blows late lead, ends season with 15-14 loss to James Madison]
The matchup with the Orange was just the beginning of Maryland’s early season tests. The Terps played four games in the following 16 days after the Syracuse game, including meetings with then-No. 7 Florida, then-No. 12 James Madison and then-No. 9 Denver.
Those games were each decided by one goal. Maryland beat Florida 14-13 in its highest-ranked victory of the season. After blowing an early lead, the Terps found themselves earning a comeback victory with a strong fourth quarter performance.
Maryland did just that. It needed to do the same against James Madison and Denver after slow starts. The Terps made strong late pushes, but the effort wasn’t enough as they lost both matchups.
The Terps made strong late pushes, but the effort wasn’t enough as they lost both matchups.
“We finally started playing hard in the fourth quarter … which is what we should have been doing all game long,” Reese said after the James Madison matchup.
Maryland’s defense began clicking as the season progressed. Its attack, however, did not.
Maryland missed Aurora Cordingley’s star power. The attacker led the team with 67 goals and 51 assists in the 2022 season. With her departure, no Terps were named Tewaaraton finalists for the first time in Reese’s 17 years as head coach.
Junior Eloise Clevenger took a big step for the Terps, posting a team-best 47 assists and 73 points. While Clevenger had a breakout year, a lack of Cordingley’s scoring output left the Terps with a big void.
Libby May’s 62 goals were on par with her 2022 performance, but nagging injuries limited Hannah Leubecker, adding salt to the wound of Cordingley’s departure.
A healthy Leubecker is a spark plug for the Terps, who missed her dodging ability and deep range. Her injuries forced players to play outside of their strengths and as dodging threats, even if that wasn’t their strong suit. May, who’s more of a catch-and-shoot cutter, was a prime example.
Her injuries forced players to play outside of their strengths and as dodging threats, even if that wasn’t their strong suit. May, who’s more of a catch-and-shoot cutter, was a prime example.
“All of our players are good at different things and we need to set each other up for success by putting them in the right spots,” Reese said.
[Former Hereford teammates to face off in Maryland, James Madison women’s lacrosse matchup]
Maryland found its groove after the losses to James Madison and Denver and won nine straight. The Terps scored at least 13 goals in each game while shooting 49 percent across the stretch.
Part of that was due to freshman midfielder Kori Edmondson’s emergence. The nation’s top-recruit recorded six consecutive hat tricks and notched three goals or more in seven of Maryland’s nine consecutive wins.
After convincing wins over then-No. 22 Rutgers, and then-No. 15 Michigan, Reese faced a threat of her first home conference loss as Maryland’s head coach from Johns Hopkins. Again, the Terps blew an early lead. Their five-goal advantage washed away in the third quarter.
Again, the Terps blew an early lead. Their five-goal advantage washed away in the third quarter.
Edmondson was the hero, hitting the dagger that extended Maryland’s winning streak.
Clevenger missed that game because of a family emergency and was listed as a game-time decision against Ohio State three days later.
Clevenger didn’t just play — she put on the best performance of her career.
The All-American broke the Terps’ single-game assist program record, dishing out eight in the winning effort. Her mom, Elizabeth “Ish” Clevenger, died the next morning after a years-long battle with breast cancer.
“It was a tough night for us, obviously a tough week,” Reese said after Maryland’s game the following week at Penn State. “It’s been a long, emotional week, but here we are, and we got a lot to learn from this game and make some changes.”
Those individual offensive performances helped the Terps string together their nine-game midseason winning streak, but their momentum came to a halt in that 12-7 loss to then-No. 18 Penn State. Maryland went 3-4 in its final seven games and the attack struggled, scoring 10.4 goals per contest on 35.4 percent shooting.
18 Penn State. Maryland went 3-4 in its final seven games and the attack struggled, scoring 10.4 goals per contest on 35.4 percent shooting.
Consistency issues throughout 2023, and eventually in its season-ending loss, led to an early exit for Maryland women’s lacrosse.
Whether it was playing a complete 60 minutes, performing well on both sides of the field or struggling to finish opportunities, Maryland never ‘put it together’ as Reese hoped. Consequently, its top-ranked win came in February instead of May, and the Terps’ hopes of a deep postseason run ended abruptly.
Keep your head warm? Is it necessary?
The materials of InoSMI contain only assessments of foreign media and do not reflect the position of the editors of InoSMI
For many years, physiologists have tried to find out exactly how people get cold. All volunteers participating in the experiment are distinguished not only by endurance, but also by hairiness (at least their heads). Lysina would add unnecessary complexity at this stage of the study. It turns out that due to the effect of cold on the head, we lose not so much heat. And what is the conclusion from this?
Lysina would add unnecessary complexity at this stage of the study. It turns out that due to the effect of cold on the head, we lose not so much heat. And what is the conclusion from this?
Claudia Hammond
To wear or not to wear, that is the question. Should I wear a hat when it gets cold? The BBC Future correspondent looked for the answer to this question in the results of immersing people in ice water and observing how the inhabitants of Patagonia warm up.
We were told that we must not capsize in our boat at any cost. Otherwise, we would only have a few seconds to get out of the water before the cold would bind us.
Here in Patagonia’s Torres del Paine National Park, toothpaste-turquoise icebergs come in every shape imaginable, from pianos to rockets.
From time to time, while we are kayaking, there are sounds of gunshots and cracking pieces of ice.
Before this trip, I had never thought about exactly how our body loses heat. Now everything I do is multiplied by hellish cold.
Now everything I do is multiplied by hellish cold.
At night, even in a tent, it chills to the bone. I sleep in a medium thickness sleeping bag with all my clothes (four pairs of pants, three brushed tops, two hats and another layer of waterproof layer).
Shivering slows down the cooling process of the body
But this is still not enough for me.
Mariano, our guide, sleeps outside with only a very thick sleeping bag to protect him from the wind.
He assures that he likes it better, and is not going to put on a hat at all.
I’m worried about him – but what about the well-known myth that the body loses most of its heat due to an uncovered head?
What the harsh experiments of Thea Pretorius showed
For many years, physiologists have tried to figure out exactly how people get cold. In this they were assisted by various groups of “guinea pigs” – from hardy students to military personnel.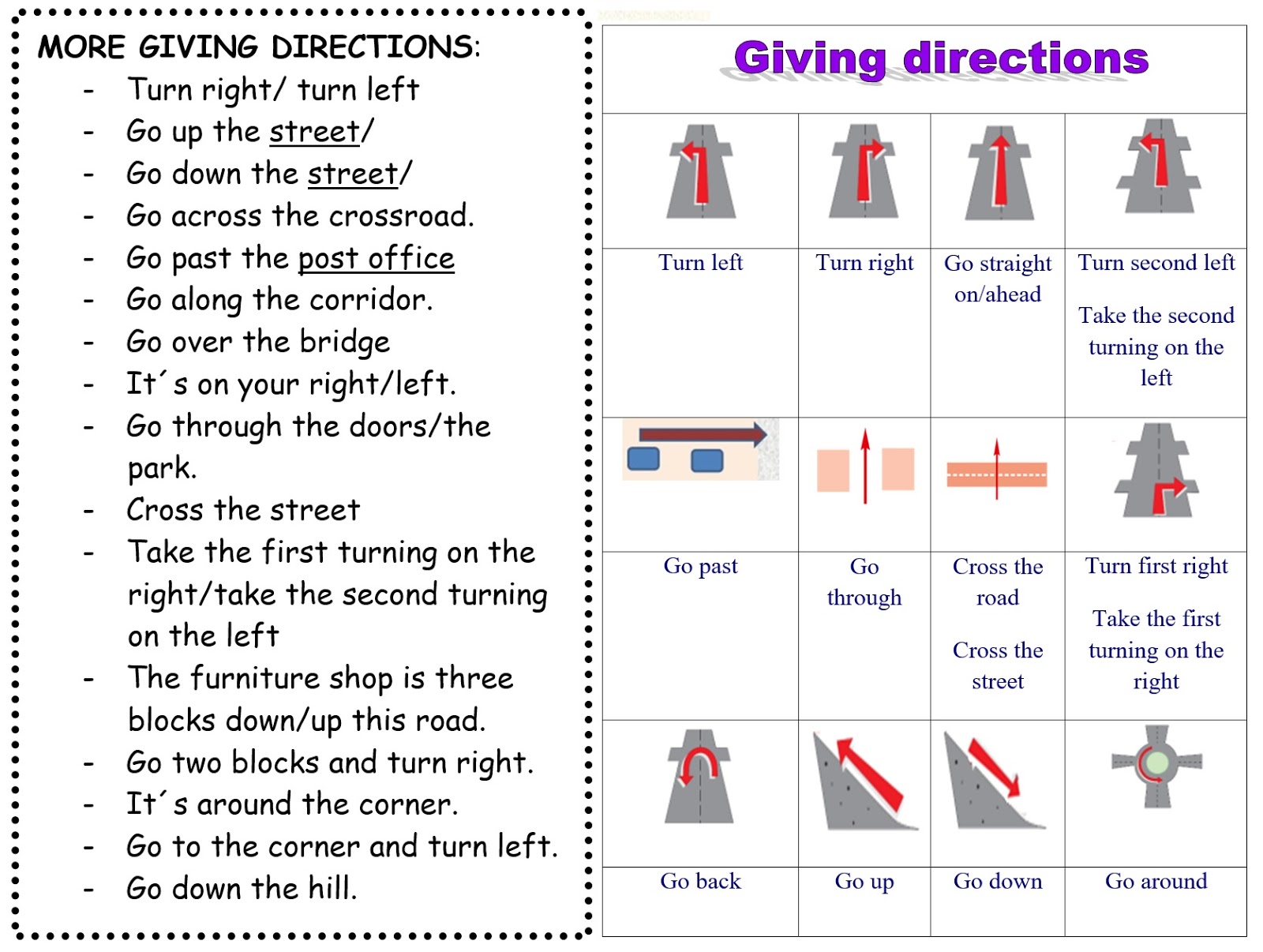
Experimentation in this area usually requires people who can tolerate a certain level of discomfort.
Thea Pretorius of the University of Manitoba in Canada uses scuba gear to gauge how much heat is escaping from the surface of her head.
Due to the effect of cold on the head, we do not lose much heat. And what is the conclusion from this?
All volunteers participating in the experiment are distinguished not only by endurance, but also by hairiness (at least their heads).
Lysina would add unnecessary complexity at this stage of the study.
In one of Thea Pretorius’ experiments, volunteers were given a substance to stop shivering (it helps the body stop heat loss).
Then the subjects were lowered into cold water on a winch. Sometimes they were completely immersed in water, sometimes their heads were left above the surface of the water.
The second variable in the experiment was the participant’s clothing: volunteers were dressed in either a bathing suit or an insulated rubber dry suit, two pairs of socks, and wool gloves. Everyone spent 45 minutes in 17-degree water.
Everyone spent 45 minutes in 17-degree water.
Immersion of the head in water increases heat loss by only 10%
As expected, volunteers lost the most heat immediately after immersion in water. However, other results of the experiment debunked popular myths.
Volunteers who immersed themselves in the water, but in waterproof suits, lost half as much heat as those who were in simple bathing suits and kept their heads above the surface of the water.
In other words, we do not lose much heat due to the effect of cold on the head.
According to the results of the experiment, immersing the head in water increases heat loss by only 10%.
This is not so much, given that the surface of the head is 7-9% of the total surface of the body.
So you don’t need a hat?
However, before you go and throw your entire collection of woolen hats in the trash, take into account one more conclusion drawn from the results of this experiment.
If the head is exposed to cold and the body is warm, the overall body temperature drops much faster than most people realize.
One of the reasons for this phenomenon is that there are a lot of blood vessels in the scalp, and all of them are especially close to the surface of the skin (because, by the way, any cut on the head leads to such profuse bleeding).
When the head is cold, people do not shiver. And this is very bad
If you put on warm clothes on a cold day but forgot to put on your hat, the air will cool the hot blood as it flows through the vessels of the scalp. Then the cooled blood returns to the body and spreads the cold.
Another reason is related to trembling. It is curious that people do not shiver when only their head is exposed to cold.
And since shivering slows down the cooling process of the body, its absence guarantees you that you will freeze much faster than with your head covered.
In extreme conditions, such as in Patagonia, the final temperature to which your body cools down plays a much greater role than how quickly it happens.
Mariano seems to have grasped this principle. He really should take care of his body temperature and keep him warm, and a hat is not so necessary. He knows from experience that he really only needs a very warm sleeping bag.
Next time I’ll take one too.
How to tighten hanging eyelids without surgery? Learn from the experts!
Article content:
- Hanging eyelids: fixing the problem
- Eyelid correction with laser
- Photorejuvenation and lifting of the skin around the eyes
Age-related changes affect the area around the eyes to a greater extent than other areas of the face. This is facilitated by the structure of the skin on the eyelids – it is mobile, thinner, tender, more easily stretched with the formation of wrinkles and swelling.
In some people, drooping eyelids are an inherited feature of appearance. But in the overwhelming majority of cases, this aesthetic problem is formed under the influence of age-related changes in the body.
Of course, a pronounced defect cannot be corrected by anything other than plastic surgery, but a mild and moderate degree of overhang can be successfully corrected by modern cosmetology techniques: photorejuvenation and laser resurfacing.
Laser correction
The main advantage of laser treatment is low trauma, coupled with an excellent aesthetic result.
Resurfacing lasts approximately 30 minutes under local anesthesia. In some cases, a second procedure may be required to achieve optimal results. However, due to the very sensitive skin of the eyelids, a single correction is usually sufficient.
During the procedure, the doctor acts on the skin with a low-intensity laser beam. Old keratinized cells “evaporate”, and in parallel with this, stimulation of the production of endogenous collagen in nearby tissues is started. The quality of the skin increases, it is tightened, which helps to eliminate the effect of the impending eyelid. The result of eyelid laser resurfacing is revealed within a few months after the procedure and lasts up to 5 years.
The result of eyelid laser resurfacing is revealed within a few months after the procedure and lasts up to 5 years.
Photorejuvenation
The photorejuvenation method of getting rid of the impending eyelid is based on the use of broadband pulsed light. The light flux, penetrating the skin to a predetermined depth, is absorbed by the collagen fibers and causes their contraction (shortening and compaction). Thus, there is a tightening of tissues, smoothing of the skin relief, reduction of excess skin.
The device for photorejuvenation allows you to change the parameters of thermal and light exposure, so discomfort and the likelihood of burns are excluded. Photorejuvenation is perfect in cases where, along with the problem of impending eyelids, there is a need to correct other aesthetic defects (pigment spots, rosacea, etc.). After the procedure, it is necessary to treat the affected area with protective creams, exclude the use of decorative cosmetics and exposure to direct sunlight.

 send()
send() For example, for
For example, for 
 example.com
example.com