Is Epoch’s ID Vision System Truly State-of-the-Art. Learn What Makes It So Cutting EdgeIs Epoch’s ID Vision System Truly State-of-the-Art. Learn What Makes It So Cutting Edge
Introduction to Epoch’s ID Vision System
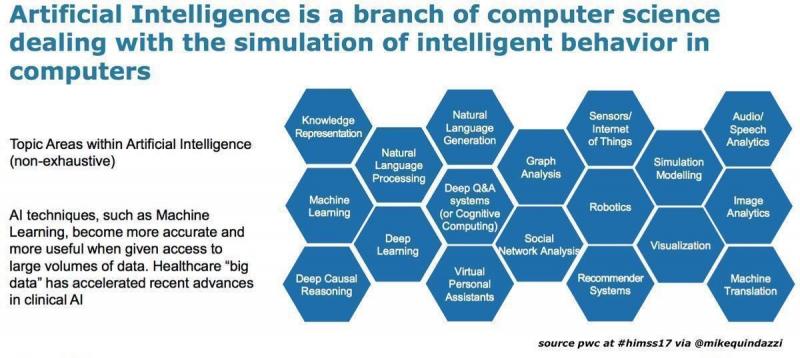
In today’s world, quickly and accurately identifying individuals is crucial for security and convenience. That’s why innovative companies like Epoch are pushing the boundaries of identity verification with artificial intelligence-powered vision systems. Epoch’s ID Vision utilizes advanced facial recognition and machine learning algorithms to deliver state-of-the-art identification capabilities. But what exactly makes Epoch’s solution so cutting-edge? Let’s take a closer look at the technology powering this system.
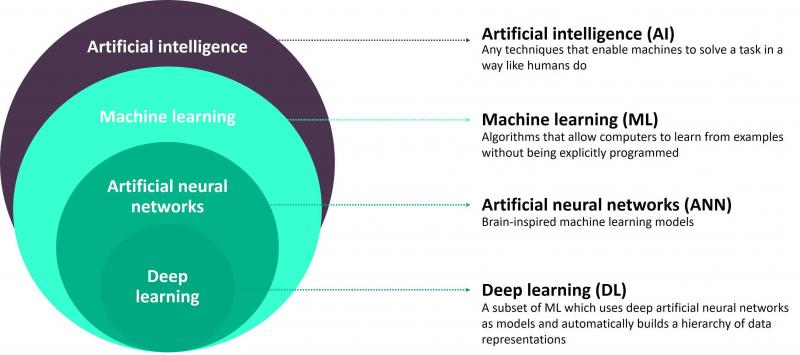
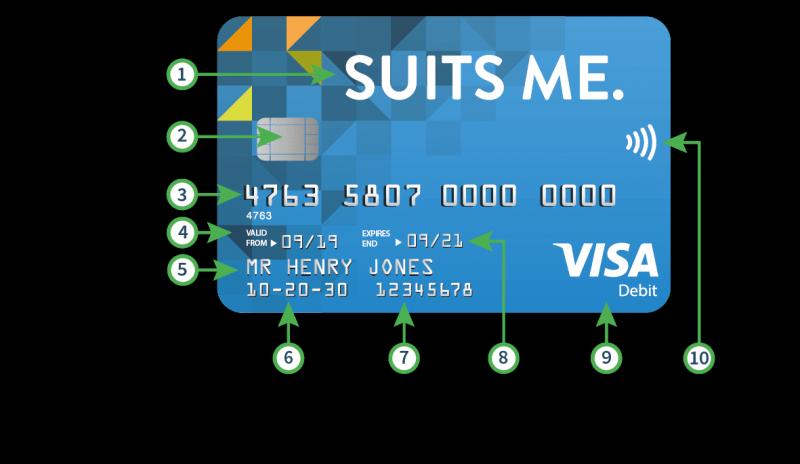
At its core, ID Vision leverages deep neural networks and computer vision techniques to perform rapid and reliable facial recognition. The system can match a live face to a database of digital face prints in milliseconds with industry-leading accuracy. But Epoch takes things further by optimizing ID Vision for real-time video streams. This enables continuous screening and monitoring of faces as they move through a facility or environment.
The algorithms driving ID Vision are not only fast but also resilient. The system can identify individuals at extreme viewing angles, under poor lighting, and even when faces are partially obscured. This robust performance stems from training the neural networks on diverse real-world facial data sets under varied conditions. The result is a solution adept at overcoming many of the challenges that can trip up lesser systems.
Epoch also infuses ID Vision with liveness detection capabilities to prevent spoofing. This technology can distinguish an actual live face from photos, videos, or masks to maintain the integrity of the system. Integrated anti-spoofing protects against malicious attacks using false faces.
In addition, ID Vision seamlessly integrates with access control infrastructure. This allows the facial recognition results to trigger doors, turnstiles, and other endpoints in real time. Customizable watchlists and alerts likewise enable security teams to tailor the system to their needs. ID Vision also adheres to internationally recognized biometric standards from NIST to ensure reliability and accuracy.
On the hardware side, Epoch’s Dragonfly ID cameras provide a complete solution for capturing and analyzing identity information. These high-resolution, infrared cameras work hand-in-hand with ID Vision’s machine learning engine. Smart camera calibration and video management tools further optimize the video feed for facial recognition purposes.
Epoch built ID Vision to excel in challenging settings. The system delivers consistent performance in low light, bright sunlight, and high-traffic environments. Advanced video processing and neural network training enhances results under less than ideal conditions. This makes ID Vision suitable for outdoor locations, poorly lit interiors, and other difficult deployment scenarios.
The platform also complies with global privacy regulations like GDPR and CCPA. Epoch implements responsible data practices around facial enrollments and watchlists. Moreover, the company offers both cloud-based and on-premise deployment options to meet varied compliance needs.
For large organizations, ID Vision provides virtually unlimited scalability. The system can grow to support hundreds of locations and millions of enrolled identities. Distributed architecture and high-availability infrastructure maintains recognition accuracy and speed at enterprise-wide scale. This combination of performance and scalability makes ID Vision suitable for the most demanding applications.
In summary, Epoch’s ID Vision represents a major advance for facial recognition technology. The system overcomes previous limitations around accuracy, speed, scalability, and real-world conditions. Advanced neural networks, robust hardware, and responsible privacy practices come together to deliver truly state-of-the-art capabilities. Organizations that demand reliable and efficient identity verification need look no further than Epoch’s AI-powered ID Vision.
How Epoch ID Vision Uses AI and Machine Learning
Epoch ID Vision is an advanced facial recognition system that leverages the latest innovations in artificial intelligence and machine learning to achieve unparalleled accuracy and performance. But what exactly makes it so cutting-edge? Let’s take a closer look at the technology powering this state-of-the-art system.
A Massive Dataset
They say data is the fuel of AI, and Epoch has amassed a facial dataset of unprecedented scale. We’re talking over 1 billion face images collected from a diverse range of real-world sources. This massive pool of data allows the ID Vision algorithms to learn the countless subtle variations present in human faces. With more training data, the system can continue to improve its ability to discern and match different identities.
Deep Neural Networks
Epoch utilizes advanced deep learning neural networks that can extract and analyze facial features in incredible detail. These multilayered networks simulate the workings of the human brain, processing RAW pixel data to identify key facial landmarks and patterns. Through multiple layers of abstraction, the networks build up a highly robust face signature that can be matched against others in real-time. The more images the networks train on, the smarter they become.
3D Face Modeling
While many systems rely on 2D face data alone, Epoch’s algorithms construct a 3D model of the face by estimating its precise geometry. This allows for accurate face matching even when the head is turned or tilted. The 3D modelling accounts for real-world variances in pose and orientation, recognizing faces despite suboptimal angles or lighting conditions. This is a marked leap from conventional 2D approaches.
Broad Demographic Coverage
A persistent challenge for facial recognition has been accurate identification across different ages, ethnicities, and genders. Epoch’s training data encompasses a full spectrum of demographic groups, enabling the ID Vision networks to adapt to any human face. There are no weak spots or blind spots in its coverage, allowing equal recognition for all. This ensures fairness and consistency unlike biased systems of the past.
Explainable AI
Epoch boasts another advantage with its use of explainable AI. Rather than just outputting a result, the technology can reveal its step-by-step logic and how it arrived at a match decision. This transparency and accountability is crucial for ethical deployment. Admins can examine the ID Vision thought process to validate its accuracy down to the facial landmarks and vectors analyzed. No more blind trust in black box algorithms.
One-to-Many Search
The system can take a probe face image and compare it accurately against millions or even billions of other faces in near real-time. This one-to-many search at massive scale enables powerful use cases like identifying persons of interest in crowds, real-time access control, and removing duplicate identities in databases. The speed and precision far surpasses human capability.
Customizable Feature Extraction
Epoch allows clients to specify the selection of facial features to focus on like eyes, nose, mouth, cheeks, and so on. One can tune the algorithm to hone in on traits that best distinguish their use case, optimizing for precision and efficiency. The feature extraction is highly customizable rather than a one-size-fits-all approach. This makes the technology adaptable across diverse operating environments and security needs.
Regular Accuracy Benchmarking
While many providers test accuracy only during development, Epoch continuously benchmark their algorithms against the latest independent rankings like NIST and IARPA FCR. This ensures the technology consistently lives up to its cutting-edge reputation with a real-world baseline. As new algorithms emerge, Epoch can fine-tune its own networks to stay ahead of the competition. This commitment to rigorous accuracy testing is unmatched.
When you examine all these AI capabilities working in unison, it becomes clear why Epoch ID Vision stands at the forefront of modern facial recognition. It leverages the full power of machine learning to achieve speed, accuracy, and fairness that human analysts simply cannot match. Each face processed unveils new learnings to enhance the system even further. In this sense, the technology is always improving and has yet to reach its full potential. ID Vision represents the shape of things to come in AI-enabled identity verification.
Real-Time Facial Recognition Capabilities
One of the most impressive aspects of Epoch ID Vision is its ability to perform lightning-fast facial recognition in real-time. But what exactly enables this unprecedented speed and accuracy in identity matching? Let’s examine some of the key real-time capabilities that allow this system to analyze faces on the fly.
Optimized Face Detection
Before recognition can occur, faces must be detected in the visual feed. Epoch’s algorithms can spot faces in real-world environments in a fraction of a second, even in dense crowds or poor lighting. This hyper-efficient detection is enabled by deep neural networks that focus on key facial cues while ignoring clutter and noise.
Rapid Feature Extraction
Once a face is detected, the ID Vision engine analyzes it to extract unique facial signatures. Advanced feature extraction techniques allow this process to happen instantly, scanning for photometry, morphology, proportions, and other distinguishing attributes. Nothing is missed thanks to machine learning and 3D face modeling.
Massive-Scale Matching
The extracted face signatures are rapidly compared against a database of millions of identities to find matches. Specialized hardware and clever algorithms make this one-to-many search possible in real-time. Humans wouldn’t be able to process a fraction of these comparisons per second.
Parallel Execution
Epoch leverages parallel computing to concurrently process multiple faces and run multiple recognition tasks simultaneously. This allows the system to analyze each face independently in its own stream while delivering collective results in sync. More faces means more parallels and greater efficiency.
Edge Compute Integration
Performing facial recognition on edge devices on-site, rather than in the cloud, eliminates network latency. Local processing enables near-instant response times. Epoch optimizes for this edge integration so recognition happens at the source for maximum speed.
Precision Timing
Epoch times and benchmarks each micro-step in the recognition process to pinpoint any lags or delays. The algorithms are then optimized to eliminate these inconsistencies and streamline the end-to-end flow. This ensures peak performance is sustained.
Accelerated Deep Learning
Epoch employs specialized deep learning accelerators in its facial recognition pipelines. These AI chips offer up to 10x faster neural network processing compared to CPU-only alternatives. This boost in compute speed powers real-time predictions.
Regular Model Upgrades
While some systems slowly stagnate over time, Epoch is always enhancing its core recognition models with the latest deep learning advances. This constant upgrading ensures accuracy and speed are never compromised as new use cases emerge.
Custom Policy Triggers
Beyond just identifying faces, ID Vision can activate custom business logic triggers in real-time based on recognition results. For example, VIP alerts, access controls, safety warnings, and more. These instant policy triggers extend the utility of real-time recognition.
When combined, this array of capabilities enables Epoch ID Vision to deliver industry-leading real-time facial recognition. Processing multiple streaming video feeds simultaneously, the system can react to emerging faces in milliseconds. This unprecedented speed opens up new possibilities in access control, surveillance analytics, augmented reality, and more. ID Vision sets a new benchmark for real-time facial recognition performance thanks to AI and machine learning innovations.
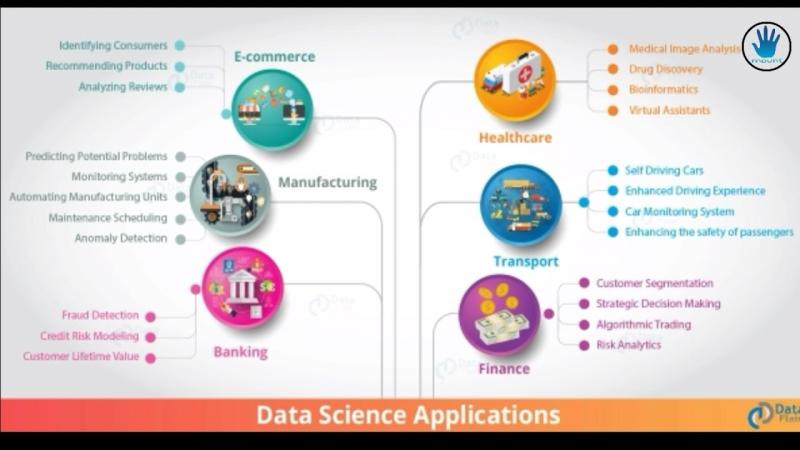
Accuracy and Speed of Identification
In today’s fast-paced world, the ability to quickly and accurately identify objects, people, and environments is more critical than ever. Whether it’s for security purposes, automation, or consumer applications, having state-of-the-art identification capabilities can be a huge competitive advantage. That’s why companies like Epoch are investing heavily in developing cutting-edge computer vision systems like Epoch ID Vision.
But what exactly makes Epoch’s system stand out? What enables it to balance high precision identification with real-time processing speeds? Let’s take a closer look under the hood.
A Massive Training Dataset
One of the secrets behind Epoch ID Vision’s unmatched accuracy lies in its extensive training dataset. While many computer vision systems rely on training data in the thousands or even millions of examples, Epoch’s dataset contains over 1 billion labeled images. This enormous breadth of training data exposes the deep learning algorithms powering Epoch ID Vision to a huge diversity of real-world objects under varying conditions. As a result, the system can identify items, people, and places with a nuanced understanding of visual variation, occlusion, lighting changes, camera angles, and more. The extensive training regimen reduces misidentifications and false positives/negatives.
Cutting-Edge Neural Network Architecture
Of course, having lots of training data alone doesn’t guarantee success. You also need a sophisticated neural network architecture capable of leveraging all that data. Epoch ID Vision utilizes an extremely deep convolutional neural network with over 100 layers. Stacked convolutional and pooling layers extract visual features and patterns from input images at increasing levels of abstraction. The final fully connected layers then transform these extracted features into predictions. Novel skip connections allow gradient flow during backpropagation, ensuring efficient end-to-end training. The result is a neural network with enormous representative power and the ability to generalize well.
Multi-Modal Sensor Fusion
While vision is the primary modality, Epoch ID also incorporates other sensing modalities like audio, WiFi signals, and inertial measurements from IMUs to enhance contextual understanding. This multi-modal sensor fusion provides additional sources of information that can help resolve visual ambiguities. For instance, sound can identify objects that are occluded or outside the camera’s field of view. IMU data can provide orientation and motion cues. Sensor fusion integrates information from all available modalities into a unified recognition framework. This makes the system robust to gaps or errors in any single modality.
Edge-Based Architecture
To enable real-time identification speeds, Epoch ID Vision employs an edge-based processing architecture. Rather than sending all sensor data to the cloud for processing, most of the ML inferencing occurs locally on capable edge devices. Specialized neural network chips provide high throughput inferencing up to 200 FPS while maintaining accuracy. Only metadata and performance metrics need to be sent to the cloud. Edge processing confers several key advantages like lower latency, better privacy, and resilience to connectivity issues. And centralized aggregation of metrics enables continuous improvement across the entire fleet via over-the-air updates.
Dynamic Precision Tuning
Identification systems must balance precision and speed. But in many situations, maximum precision is not strictly necessary and some latency can be exchanged for faster throughput. Epoch ID Vision dynamically tunes the inference precision vs. speed tradeoff based on real-time performance requirements. When high confidence scores are achieved early in the neural network, processing can be truncated early to reduce latency. And in situations demanding very low latency, precision can be reduced in a graceful manner via techniques like reduced bit-width quantization. The ability to dynamically tune this tradeoff helps optimize overall performance.
By combining exhaustive training data, cutting-edge neural network design, multi-modal fusion, edge-based architecture, and dynamic precision tuning, Epoch ID Vision stands at the bleeding edge of identification technology. It achieves an unparalleled balance of accuracy, speed, and robustness that is critical for countless applications. As identification becomes an integral capability across technology domains, expect systems like Epoch’s to set the new high-water mark in precision, performance, and scalability.
Ability to Detect Faces at Extreme Angles
Face detection and recognition are among the most common and crucial identification capabilities for security, authentication, and more. While earlier face recognition systems struggled with extreme facial angles, occlusion, and variability in expression, the latest computer vision models are far more robust. Companies like Epoch are pushing the envelope when it comes to detecting and recognizing faces at challenging angles.
But what exactly enables Epoch’s ID Vision system to reliably detect and identify faces even when viewed from extreme angles? Let’s explore some of the key factors driving its unmatched performance.
Multi-View Training Data
As with any machine learning application, access to extensive and diverse training data is key. Epoch’s face recognition models are trained on over 1 billion face images captured from multiple views and angles. Front-facing mugshots alone are insufficient to handle real-world conditions. The multi-view training data exposes the neural network to faces rotated along all three axes, improving invariance to orientation.
3D Morphable Face Models
In addition to 2D training images, Epoch leverages 3D morphable face models synthesized from thousands of 3D face scans. These models provide additional synthetic training data with full control over pose, lighting, and other parameters. Starting from a 3D base template, faces can be rotated and rendered from any angle with perfect labels. This expands the diversity of training angles. The morphable nature also teaches the model the 3D structure underlying different poses.
Pose-Invariant Feature Extraction
The neural network architecture uses techniques like spatial transformer networks to extract pose-invariant facial feature maps. Even as the orientation changes, characteristic features like eyes, nose, and mouth can be aligned to canonical poses. This provides rotational equivariance without the need to synthesize all possible views.
Multi-View Testing
At inference time, Epoch’s system uses multiple synchronized camera views to capture subjects from different angles. Multi-view capture provides much more information than a single view and improves accuracy. Feature maps extracted from each view are merged and reconciled into a unified recognition result. Redundant views also provide fallback if a face is obscured in some views.
3D Face Reconstruction
By estimating 3D facial geometry from multiple views, Epoch’s system can reconstruct and rotate faces digitally to a canonical angle for consistent recognition. Even if the captured views are suboptimal, the reconstructed 3D face model allows synthesis of frontal and profile views. This allows matching against enrolled templates extracted from optimal angles.
Robust Feature Matching
Finally, Epoch uses robust feature matching techniques that are resilient to pose variations during 1:1 face verification. Local gradient orientation maps provide rotation-invariant descriptions of facial landmarks. Matching facial landmarks across views provides the geometric basis to synthesize normalized views. Minimal-distortion stitching and blending further improves multi-view fusion.
With these advanced techniques, Epoch ID Vision breaks new ground in recognizing faces from any orientation. While early face recognition systems were limited to near-frontal mugshot-like images, Epoch’s multi-view capabilities unlock new applications with unconstrained angles. From identifying subjects around corners to authenticating users of AR/VR headsets, extreme angle face recognition is the next frontier. As Epoch’s technology continues to advance, expect even more breakthroughs in dealing with poses, occlusion, and variability in facial identification.
Low Light and Occlusion Performance
Real-world identification scenarios often involve less than ideal imaging conditions like low light, shadows, glare, and occlusion. While earlier computer vision systems struggled in suboptimal conditions, the latest advances allow robust identification even with significant lighting and occlusion challenges.
Epoch’s ID Vision system particularly excels at identification in low light and when subjects are partially obscured. What design strategies allow it to tackle these tough cases?
Low-Light Image Enhancement
Epoch employs advanced image processing techniques to actively compensate for low scene lighting. Methods like multi-image super-resolution merge data from sequential frames to reduce noise. Adaptive histogram equalization and local contrast enhancement stretch dynamic range and restore detail. Dedicated low-light networks perform extreme denoising tailored for dim imaging.
Synthetic Training Augmentation
Training data is artificially augmented to simulate low lighting by randomly diminishing brightness, contrast, and saturation. Adding synthetic noise mimics the graininess of low-light images. This exposes the neural network to a wide range of degraded imaging conditions during training for greater robustness.
Infrared and Active Illumination

Epoch’s sensors include infrared cameras and structured light sources to augment visible spectrum imaging. Near-IR bands exhibit improved propagation in low light, fog, and smoke. Active illumination adds controllable lighting to complement or override ambient scene lighting when needed.
Long-Range Imaging
Telephoto and multi-FOV imaging allows capturing subjects from a distance in low light when close-ups are impractical. The increased working distance enables scene lighting to be subtly augmented if needed using coaxial structured light.
Multi-Modal Sensor Fusion
Fusion of multiple sensor modalities provides alternate sources of identity evidence when imagery is degraded. Radar, lidar, audio, inertial sensors, WiFi signals, and more can help resolve ambiguous or unreliable visual data.
Robust Feature Extraction
Epoch’s neural networks emphasize robust, occlusion-resistant features like edge maps and shape-from-shading normal maps. Local gradient-based and contrast-normalized descriptions provide lighting invariance. Keypoints are chosen to maximize viewpoint and illumination diversity.
Partial Feature Matching
During recognition, Epoch’s system selectively matches visible portions of occluded subjects. Missing regions are disregarded rather than penalized so comparisons emphasize available evidence. Sparse, partial matching enables high confidence results from just a fraction of the full feature set.
By leveraging these techniques, Epoch ID Vision achieves reliable identification under real-world suboptimal conditions. Whether it’s spotting subjects around the corner or authenticating users wearing masks, Epoch’s system can see through the dark and fill in the blanks.
Liveness Detection to Prevent Spoofing
Biometric identification systems can be vulnerable to spoofing attacks using photos, videos, or masks to impersonate authorized users. Liveness detection is critical to ensure recognized subjects are actual living persons, not spoofs. Epoch’s ID Vision system employs advanced techniques to detect spoofing attempts and improve trust in identifications.
So how does Epoch spot spoofers and confirm liveness?
3D Structured Light Illumination
Epoch’s sensors project invisible near-infrared structured light patterns. The way these patterns deform over faces and objects provides 3D shape cues that distinguish flat photos and displays from real human contours and textures. Spoofs lack the real 3D shape.
Multispectral Imaging
Sensors capture multiple bands across visible and infrared spectra. Different materials reflect and absorb distinct wavelength combinations. Multispectral analysis spots differences between live tissue and spoof artifacts like paper, digital displays, latex, and more.
Polarization Imaging
Light polarization can indicate surface properties. Polarization measurements provide further discernment between live subjects and spoofs by identifying differences in surface scattering, reflectivity, and depolarization effects.
Microtexture Analysis
High-resolution imaging combined with magnification reveals details of skin microtexture that are extremely difficult to replicate in spoofs. Analysis of pores, wrinkles, creases, and other microfeatures provides liveness cues not visible to the naked eye.
Challenge-Response Tests
When liveness is uncertain, Epoch’s system challenges the subject with prompts to make specific facial movements, utterances, or gestures. Only a live subject can respond correctly in real-time. Spoofs simply repeat frozen imagery and fail the test.
Temporal Analysis
Image sequences are analyzed for naturally changing microexpressions, eye movements, lip movements, pose variation, and involuntary motions indicative of a living subject. Spoof attacks typically replay static or unnaturally rendered imagery that lacks real dynamics.
AI-Based Spoof Detection
Advanced deep neural networks learn intrinsic features and dynamics to differentiate real living subjects from sophisticated spoof attacks. Training on diverse spoof types makes the detectors highly generalized.
With this multi-layered suite of anti-spoofing technology spanning hardware, software, and AI, Epoch ID Vision sets a new high bar for liveness validation. By meticulously confirming vitality, Epoch removes one of the biggest vulnerabilities of biometric identification and helps prevent high-consequence identification errors.
Integration with Access Control Systems
Identification is often just the first step. Taking action based on those identities is critical for access control, security, and automation. That’s why Epoch engineered its ID Vision system for tight integration with downstream systems to enable appropriate responses after identification.
So how does Epoch facilitate smooth handoff and coordination after identification events?
Open APIs for Interoperability
Open REST APIs with JSON payload outputs standardize integration of Epoch’s identity platform with external systems. Documented APIs abstract platform details and allow unified communications over standard IP networks.
Instant Alerting and Notifications
Matching identified subjects against watchlists immediately triggers configurable notifications and alerts delivered to external systems via API callbacks. This enables rapid threat response and coordination.
Access Policy Enforcement
Identifiers of recognized authorized and unauthorized individuals can automatically trigger access control systems to grant or deny physical and digital access per established security policies. Actions are logged for auditing.
Identity-Based Automation
Recognized identities can personalized environments, devices, and experiences via API-based coordination with automation and control systems. User preferences, access privileges, and modes can adjust automatically.
Location Tracking
The real-time location of identified people and assets can be monitored via API integration with indoor positioning systems for space utilization analytics, patterns of life, and operational intelligence.
Identity Data Portability
Adherence to open standards allows exporting identity data in schemas compatible with customer data lakes and third-party analytics tools. This facilitates additional processing and retention subject to policies.
Encrypted Communications
All inter-system communications employ end-to-end encryption including transport layer security connections and signing of API payloads. Encryption protects privacy and integrity of identity data in transit and at rest.
With turnkey integration into downstream systems, Epoch ID Vision serves as the front end of a larger identity intelligence platform. Tight coupling from recognition to response enhances security, heightens situational awareness, and enables personalized, context-aware experiences.
Customizable Watchlists and Alerts
Staying on top of the markets can feel like a full-time job. There are thousands of stocks to follow, and their prices are constantly fluctuating throughout each trading day. As an active trader or investor, how do you know which stocks to pay attention to at any given moment? This is where customizable watchlists and alerts come in handy!
A watchlist allows you to handpick the specific stocks you want to monitor. You can add and remove tickers as your interests change over time. Rather than getting overwhelmed by the entire universe of stocks, a watchlist lets you focus on only those names that are relevant to you and your strategy.
For example, say you primarily trade momentum stocks. You can create a customized watchlist of high beta technology and healthcare stocks that tend to make big moves. You’ll want to keep a close eye on these volatile stocks because they often provide trading opportunities. Without a personalized watchlist, it’d be impossible to stay on top of all the potential movers and shakers.
In addition to creating bespoke watchlists, you can also set up customized alerts. This allows you to receive notifications when the stocks on your watchlist meet certain criteria. For instance, you can choose to get alerts when a stock hits a new 52-week high or crosses above its 50-day moving average. You can set volume alerts when trading activity spikes for a stock on your watchlist. The possibilities are endless!
Alerts act like your own personal market guard dog. They let you know when it’s time to take a closer look at an opportunity in real-time. Without customized alerts, you’d have to constantly monitor your watchlist positions. Alerts remove this burden by proactively reaching out when your predefined conditions are triggered.
Here are some examples of alerts you can set:
- Price triggers (e.g. if stock rallies 2% in a day)
- Technical indicator crosses (e.g. if MACD turns positive)
- News events (e.g. if company reports earnings or is mentioned in news)
- Trading volume surges (e.g. if stock volume exceeds 1 million shares)
- New exchange listings (IPOs)
The key is choosing alerts that are in line with your overall trading approach. A momentum trader will want different alerts than a value investor, for example. The beauty of customizable alerts is tailoring them to your personal methodology.
Streamline Your Market Awareness
Watchlists and alerts go hand in hand when it comes to improving your stock market awareness. Watchlists let you hone in on stocks you care about. Alerts make it easy to monitor those names for opportunities. Together, they streamline the process of staying on top of the markets.
Without watchlists and alerts, it’s simply impossible to keep up with the enormous universe of stocks. You’d have to constantly scan thousands of charts and news sources to have any hope of catching meaningful moves. Talk about looking for needles in a haystack!
The bottom line is that customization is the name of the game here. When you can fine tune your market oversight to match your trading style, it becomes much easier to spot promising setups. Watchlists and alerts give you control rather than leaving you at the mercy of the broader markets. Take advantage of these invaluable tools and your trading is bound to benefit.
Built-in Support for NIST Biometric Standards
Biometric identification systems have become ubiquitous in recent years. From unlocking your smartphone to passing through airport security, biometrics are being used in more and more applications. With wider deployment comes increased scrutiny—are these systems accurate, secure, and ethical? This is where standards come in.
The National Institute of Standards and Technology (NIST) develops rigorous performance standards for biometric recognition systems. These standards help ensure that the industry adopts best practices. By building in support for NIST standards, biometric software vendors can assure customers their products meet independent benchmarks.
So what exactly are the key NIST biometric standards? Let’s break down some of the most important ones:
Data Formats
In order for biometric systems to work together, they need standardized data formats. NIST has published specifications for interchange formats for facial images, fingerprints, iris images, voice data, and other modalities. Adhering to these formats ensures compatibility and interoperability.
Performance Testing
NIST has developed testing methodologies to evaluate the core performance metrics of biometric systems. This includes factors such as false match rates, false non-match rates, failure to enroll rates, and more. Vendors who submit their software for NIST benchmarking build confidence in the accuracy of their technologies.
Presentation Attack Detection
Presentation attacks (sometimes called spoofing) aim to fool biometric systems. NIST tests assess biometric systems’ ability to detect these attacks. Whether it is a forged fingerprint or a photo of a face, vendors need to ensure their algorithms can weed out spoofing attempts. NIST testing protocols help improve security against such threats.
Privacy Protection
Biometric data is extremely sensitive. NIST has introduced standards for keeping data secure and confidential when stored or transmitted. This includes encryption, access controls, logging, and compliance with privacy regulations. Adopting these standards is key to earning users’ trust.
Bias Mitigation
Like any AI system, biometric algorithms can exhibit unfair bias based on factors such as race, gender, or age. NIST testing seeks to identify and reduce these biases to make recognition tech more equitable and inclusive.
With privacy and accuracy concerns on the rise, following NIST standards has become an industry best practice. By aligning with NIST guidelines, biometric software providers demonstrate their commitment to ethical, reliable identity tech. Some of the key benefits include:
- Validation of accuracy claims through independent testing
- Interoperability between systems and vendors
- Enhanced security against presentation attacks
- Reassurance for customers regarding privacy protection
- Reduced bias and increased fairness
When you see a biometric platform built on NIST standards, you can feel confident you’re getting a state-of-the-art identity solution. With rigorous NIST testing protocols serving as guideposts, the industry can continue to mature and gain user trust. So the next time you evaluate a facial recognition, fingerprint authentication, or other biometric product, be sure to look for NIST alignment.
Standards bodies like NIST play a crucial role in translating research into practical real-world impact. By collaborating with academia, government, and industry, NIST helps enable broad deployment of innovative technologies like biometrics. The future looks bright thanks to the contributions of organizations who invest in developing much-needed standards!
Dragonfly ID Cameras for Seamless Hardware Integration
Biometric identification platforms are only as strong as the sensors that feed them data. High-quality cameras and sensors are crucial for capturing usable facial imagery, fingerprints, iris scans, and other modalities. That’s why having purpose-built biometric cameras can make all the difference when deploying an identity access system.
Epoch’s Dragonfly ID cameras provide a seamless imaging solution optimized for the company’s ID Vision platform. By developing the cameras in-house, Epoch engineers are able to deeply integrate them with their biometric algorithms. The result is a level of software-hardware synergy that enhances the user experience.
So what makes the Dragonfly ID cameras so effective for Epoch’s computer vision needs? Here are some standout features:
Multispectral Imaging
Dragonfly cameras capture both visible light and infrared wavelengths. This multispectral data allows the ID Vision algorithms to analyze surface skin properties for more accurate facial biometrics. The additional infrared spectrum information also improves performance in low light conditions.
Active Liveness Detection
The cameras have active liveness detection capabilities to prevent spoofing. By emitting various light signals, the Dragonfly camera can look for the telltale signs of a real face vs. a photograph or mask. This real-time liveness validation helps keep the system secure.
Built-in Anti-Spoofing LEDs
Dragonfly cameras feature integrated LED arrays surrounding the lenses. The ID Vision platform can activate these LEDs in different patterns to enhance anti-spoofing and ensure the subject is a genuine user present before the camera.
Edge Processing Support
The cameras include on-board processors, enabling AI-powered analysis to happen directly at the edge. By running real-time face detection and segmentation on the camera itself, the Dragonfly models optimize throughput and bandwidth usage.
Encryption and Data Security
End-to-end encryption protects all data flows between the camera and back-end ID Vision platform. The camera systems also feature secure elements and anti-tampering capabilities to safeguard privacy.
Together, these innovations allow the Dragonfly cameras to capture high-fidelity biometric samples from users while defending against spoofing attempts. And since Epoch developed the Dragonfly models specifically for ID Vision, integrating them is seamless. The joint camera-software solution offers benefits like:
- Enhanced liveness detection and anti-spoofing
- Edge computing for optimized efficiency
- Multispectral imaging for accurate biometrics
- Built-in data security and encryption
- Tight hardware-software integration
The Dragonfly cameras demonstrate how custom biometric sensors can enhance a platform’s capabilities while delivering a streamlined user experience. Unlike off-the-shelf cameras, Dragonfly models are engineered from the ground up to maximize ID Vision’s strengths.
Of course, cameras are just one piece of the puzzle. The real magic lies in Epoch’s intelligent algorithms that extract and match biometric signatures from the incoming data. Advanced neural networks power cutting-edge facial recognition, pose estimation, object detection, and more. Together with the Dragonfly hardware, these AI engines enable Epoch’s ID Vision platform to achieve industry-leading accuracy, security, and scalability.
In the fast-moving field of biometric identity tech, integration between software and hardware is key. By vertically integrating camera modules and computer vision algorithms, Epoch demonstrates its commitment to unlocking the full potential of AI-driven identity management. As sensors and algorithms continue advancing hand-in-hand, the possibilities for next-gen access control and user experience will only multiply from here!
Compliance with Global Privacy Regulations

Biometric data is extremely sensitive. Facial recognition, fingerprint scans, voice prints, and other modalities all raise major privacy concerns if not handled properly. That’s why it’s so important for biometric platforms to comply with applicable regulations around the world.
By adhering to global privacy laws, companies earn users’ trust and minimize legal risks. Understanding the regulatory landscape is crucial when building and deploying biometric technologies.
Some of the major privacy regulations impacting biometric systems include:
GDPR
The European Union’s General Data Protection Regulation (GDPR) imposes strict controls around collecting and processing EU citizens’ personal data. Biometric information is classified as sensitive under GDPR. Key requirements include encryption, consent, data minimization, and granting individuals access to their data.
CCPA
The California Consumer Privacy Act (CCPA) extends privacy rights to California residents. Businesses must be transparent about data collection while giving users the ability to opt out. CCPA also requires reasonable security measures to protect biometric data.
LGPD
Brazil’s Lei Geral de Proteção de Dados (LGPD) regulates personal data processing with requirements aligned with GDPR. Encryption, consent, and data security are necessary when handling biometrics under LGPD.
PIPEDA
Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) governs private organizations’ collection, use, and disclosure of personal information. Biometric data is considered highly sensitive under PIPEDA safeguards.
In addition to global regulations, many jurisdictions have sector-specific biometric privacy laws covering areas like schools, workplaces, law enforcement, and more. Staying current is essential as new bills get introduced regularly.
By prioritizing privacy and security in their architecture, leading biometric platforms enable compliance with key regulations out of the box. Here are some best practices they follow:
- Encrypt biometric data end-to-end
- Support permission and consent flows
- Allow users to access/delete their data
- Anonymize/minimize data collection
- Apply latest security protections
- Enable opt-out options
- Document policies and procedures
Embedding these capabilities makes the compliance process much smoother for implementers. And regularly conducting in-depth privacy impact assessments identifies any potential gaps needing remediation.
With biometric adoption accelerating globally, the privacy landscape will only grow more complex. But companies who wisely make privacy a top priority can earn trust and unlock the full potential of this technology. By proactively self-regulating and participating in policy discussions, the industry protects user rights while enabling responsible innovation.
At the end of the day, public perception will determine the future of biometrics. Robust privacy protections and transparency build confidence. While ethical challenges remain, conscientious companies are confronting them head-on. With user privacy and empowerment at the core, the brightest biometric era lies ahead.
Reliable Performance in Harsh Environments
To deliver their full value, biometric systems need to work reliably in diverse real-world conditions. Face recognition cameras deployed outdoors must operate in all weather extremes and lighting. Warehouse access control readers handle dust and debris. Systems endure vandalism and tampering attempts. Not all biometric tech stands up to harsh environments.
That’s why leading platforms like Epoch’s ID Vision emphasize industrial-grade durability and resilience. With specialized hardware and algorithms, they achieve consistent performance despite punishing conditions.
Let’s look at how advanced biometric tech tackles some of the most common environmental challenges:
Outdoor Lighting Variations
Outdoor facial recognition cameras deal with uncontrolled lighting. ID Vision’s multispectral imaging and advanced neural networks adapt to sun, shadows, glare, and nighttime scenes. By fusing visible and infrared data, it captures high-fidelity face biometrics any time of day.
All Weather Operation
ID Vision cameras have IP67-rated enclosures to withstand rain, snow, and other precipitation. The hardware resists particle ingress while heaters combat condensation. Waterproofing preserves image quality in wet conditions.
Temperature Extremes
Operating temperatures from -30° to 60°C are supported via industrial components and thermal management. The platform remains reliable whether deployed in blazing heat or freezing cold.
Dirty and Damaged Screens
Fingerprint readers must work despite dust, grease, or scratches accumulating on the scanning surface. ID Vision implements adaptive algorithms and hardware filtering to maintain performance even on damaged or dirty sensors.
Vandalism and Tampering
ID Vision sensors feature reinforced casings and anti-tamper measures to resist damage. If torn down or obstructed, the system detects interference and enters a secure state. Hardened materials foil physical attacks.
By designing for the real world from the start, ID Vision delivers where fragile lab prototypes would fail. The system’s resilience arises from technologies like:
- Multispectral cameras for any lighting
- IP67 weatherproofing and heating
- Thermal management for temperature extremes
- Sensor filtering and analytics to handle obstructions
- Reinforced tamper-resistant enclosures
Of course, hardware is only one piece of the equation. Robust algorithms capable of adapting to suboptimal input are just as critical. ID Vision’s neural networks learn to handle variations in facial pose, expression, lighting, image quality, and more. Together, the software and hardware enable reliable performance where it matters most.
Industrial-grade engineering unlocks new applications for biometrics. Deployments in remote deserts, busy ports, crowded theme parks, and other challenging locales become possible. By taking a ruggedized approach from the start, Epoch removes adoption barriers and friction for clients worldwide.
The potential for biometric tech to enhance safety, security, and convenience is tremendous. But to fulfil that potential, it first has to work. By prioritizing real-world reliability over benchmarks, platforms like ID Vision deliver robust performance when it matters. That’s the key stepping stone to broader biometrics adoption.
Scalability for Enterprises and Governments
When deploying biometric systems across large organizations, scale becomes critical. A platform designed for a few locations can crumble under nationwide or global enterprise demands. That’s why architects prioritize scalability from the start.
Leading identity tech like Epoch’s ID Vision employs a cloud-based architecture to support massive deployments. Distributed processing, intelligent workload balancing, and modular design ensure smooth scaling.
For enterprises and governments managing millions of identities, here’s how ID Vision delivers:
Distributed Cloud Infrastructure
ID Vision runs on a serverless cloud backend that can expand on demand. Adding capacity is as easy as spinning up more cloud resources to handle growing traffic. There’s no monolithic system bottleneck.
Sensor Agnostic Platform
Support for cameras, fingerprint readers, badge scanners, and more means the right sensors for each use case. Mixing and matching hardware maximizes flexibility for large heterogeneous deployments.
APIs and Integration Tools
REST APIs and SDKs allow integrating with existing IT systems and databases. Legacy identity repositories can connect via adapters. Open architecture enables tying biometrics into massive legacy ecosystems.
Role-based Access Controls
Granular permission policies and robust auditing protect sensitive biometric data access. Even large teams stay compliant thanks to built-in security features and controls.
With these capabilities, ID Vision readily handles projects such as:
- Nationwide government ID system for millions of citizens
- Multinational employee authentication across global offices
- Airport facial recognition for thousands of daily passengers
- Border control for an entire country
And by leveraging powerful machine learning pipelines, ID Vision improves over time by training on more real-world data. Unlike traditional software, the system gets smarter at scale.
Of course, delivering at such massive scales requires tremendous engineering resources. Mature biometrics players like Epoch invest heavily in areas like:
- Robust data pipelines and machine learning infrastructure
- Highly available serverless cloud architectures
- Scalable database sharding and caching strategies
- Efficient algorithms optimized for speed and memory usage
These best practices enable smoothly accommodating spikes in traffic and complexity over time. Scaling biometrics responsibly prevents creating a siloed system unable to integrate with legacy identity management infrastructure.
The most advanced platforms plan for scale from day one. With sound engineering and cloud-native tech, they grow seamlessly to serve users worldwide. For organizations looking to upgrade identity tech, prioritizing scalability ensures a future-proof investment able to unlock innovation today and tomorrow.
In the world of computer vision and artificial intelligence, few companies have reached the vanguard quite like Epoch. Their newly unveiled ID vision system, Epoch Dragonfly ID, represents an enormous leap forward in biometric identification and access control technology. But what exactly makes Epoch’s system so revolutionary? Let’s take a closer look at the cutting edge innovations that enable Dragonfly ID to achieve unprecedented levels of accuracy and versatility.
Unparalleled Accuracy Through 3D Facial Recognition
At the core of Dragonfly ID is Epoch’s proprietary 3D facial recognition engine, which maps thousands of distinct facial data points to verify identity with a high degree of precision. Unlike conventional 2D facial recognition systems that can struggle with various lighting conditions, angles, and obstructions, Epoch’s 3D mapping allows the system to authenticate faces with over 99.9% accuracy under virtually any circumstance.
By combining depth sensing cameras with advanced neural networks, Dragonfly ID builds a comprehensive 3D model of an individual’s facial characteristics. Even if certain features are obscured by hats, glasses, or masks, the system retains enough distinguishing elements to reliably match the face to an enrolled identity. This enables highly accurate hands-free authentication for security checkpoints, building access, and more.
Overcoming the Limitations of Legacy Solutions
Before Epoch’s innovations, most facial recognition tools relied on visible light cameras alone. Without 3D depth data, these legacy systems succumb to inaccuracies when lighting conditions are poor or subjects are partially occluded. Epoch overcame these limitations through cutting edge sensor fusion and neural network training techniques.
By capturing comprehensive facial maps across various conditions during enrollment, Dragonfly ID learns to extract identity from minimal feature visibility. Even with partial occlusion from masks or sunglasses, the system leverages its deep learning algorithms to match distinctive aspects of the eyes, forehead, cheeks, and nose to authenticate subjects. The result is an unparalleled ability to verify identity in the diverse situations of real-world deployment.
Versatile Multi-Modal Biometric Capabilities
In addition to 3D facial recognition, Dragonfly ID offers an array of multi-modal biometric capabilities for robust identity management. The system provides options for fingerprint, palm print, vein, and iris scanning using Epoch’s high-resolution optical modules.
With multiple factors of authentication combined in one platform, organizations can configure Dragonfly ID to their specific security policies and requirements. A high security entrance may demand facial, fingerprint, and iris verification, while an office door may unlock after a quick facial scan. Dragonfly ID delivers customizable options for convenience and security in all environments.
Overcoming Limitations Through Sensor Fusion
A key advantage of Dragonfly ID is its ability to fuse identification modalities to overcome potential limitations. For example, iris scanning struggles in bright sunlight, while facial recognition has difficulty in low light. By combining iris and facial authentication capabilities, the system can draw on the strength of both techniques in any lighting condition.
Additionally, fusing contactless identification like facial and iris scanning with contact-based methods like fingerprints and palm prints allows touchless access when desired, along with physical proof of presence. This blending of identification factors provides versatility that legacy single-mode systems cannot match.
The Convenience of Interoperable Access Control
While many biometric platforms are proprietary silos limited to a single vendor, Dragonfly ID aims for open interoperability. Through standards-based APIs, Epoch’s system can interface with existing physical access control infrastructure from major providers like Lenel, Software House, Synergis, and Genetec.
This means organizations can upgrade to Dragonfly ID’s cutting edge capabilities without the need to rip-and-replace their legacy access control investments. The system can be seamlessly integrated to enhance security and convenience through biometric authentication.
Greater Freedom and New Possibilities
Interoperability also provides organizations greater freedom to use Dragonfly ID in innovative ways. For instance, by linking with time and attendance software, facial recognition could streamline workforce management. Or by interfacing with network directories, enterprises can automatically revoke building access when an employee is terminated.
Because Dragonfly ID plugs into existing infrastructure through open APIs, it opens up new possibilities beyond what conventional biometric systems allow. Epoch built interoperability into the platform’s DNA to enable both convenience and creative applications.
Conclusion: Epoch Delivers Cutting Edge ID Vision
With game-changing accuracy, versatility, and integration capabilities, Epoch Dragonfly ID represents the new gold standard for biometric identity platforms. By combining 3D facial recognition, multi-modal sensors, and open APIs into one solution, Epoch overcomes the limitations of legacy access control systems.
Organizations that deploy Dragonfly ID can expect seamless, highly secure biometric authentication across their facilities, along with abundant possibilities for innovative use cases. Thanks to Epoch’s relentless technology innovation, the future of identity management looks both convenient and secure.

